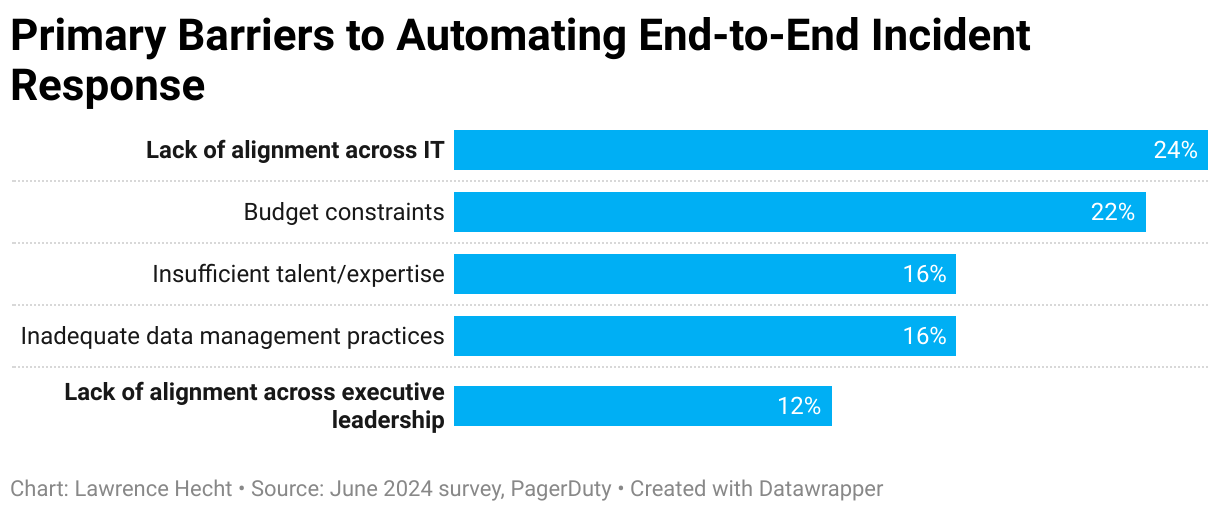
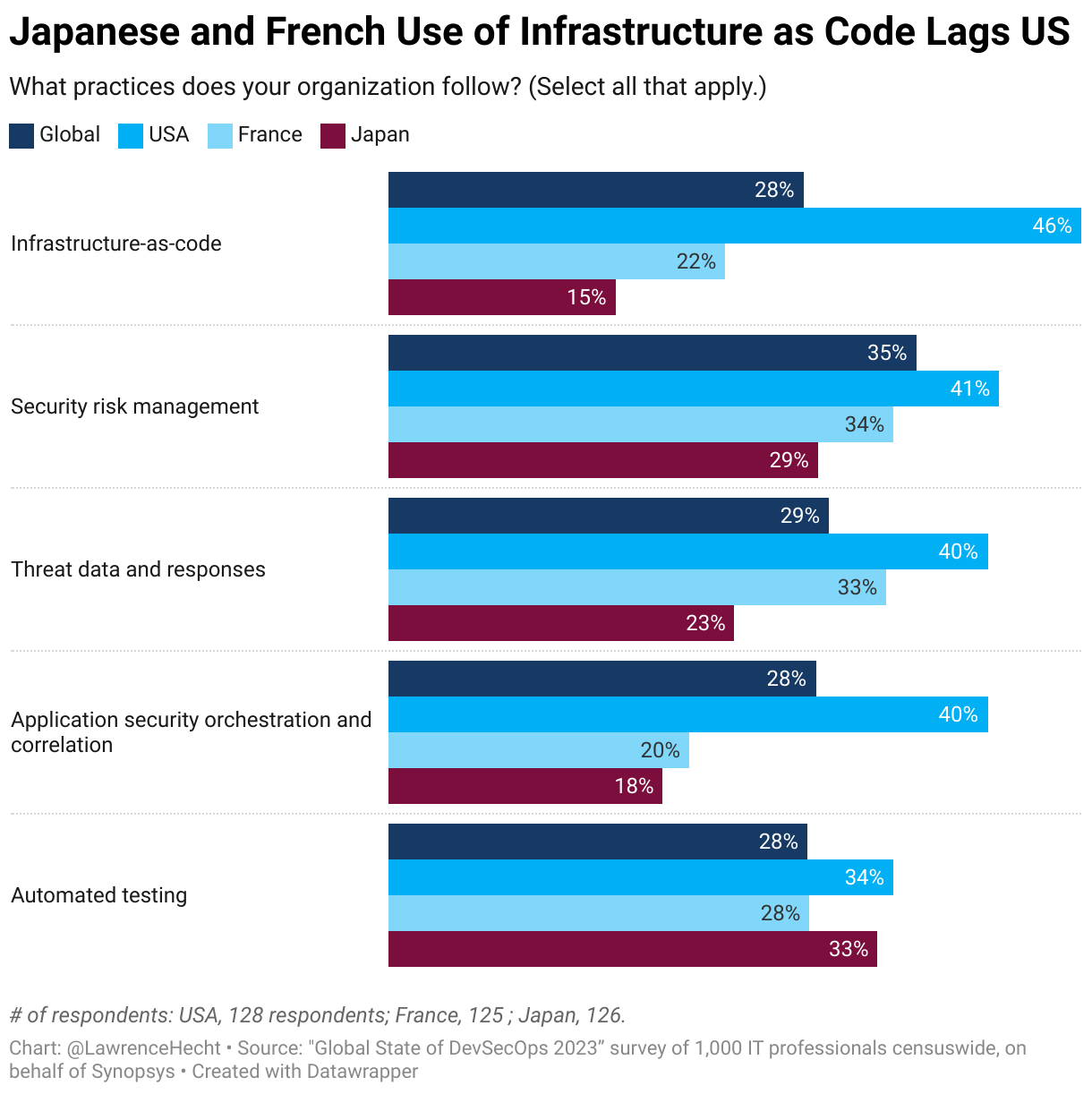
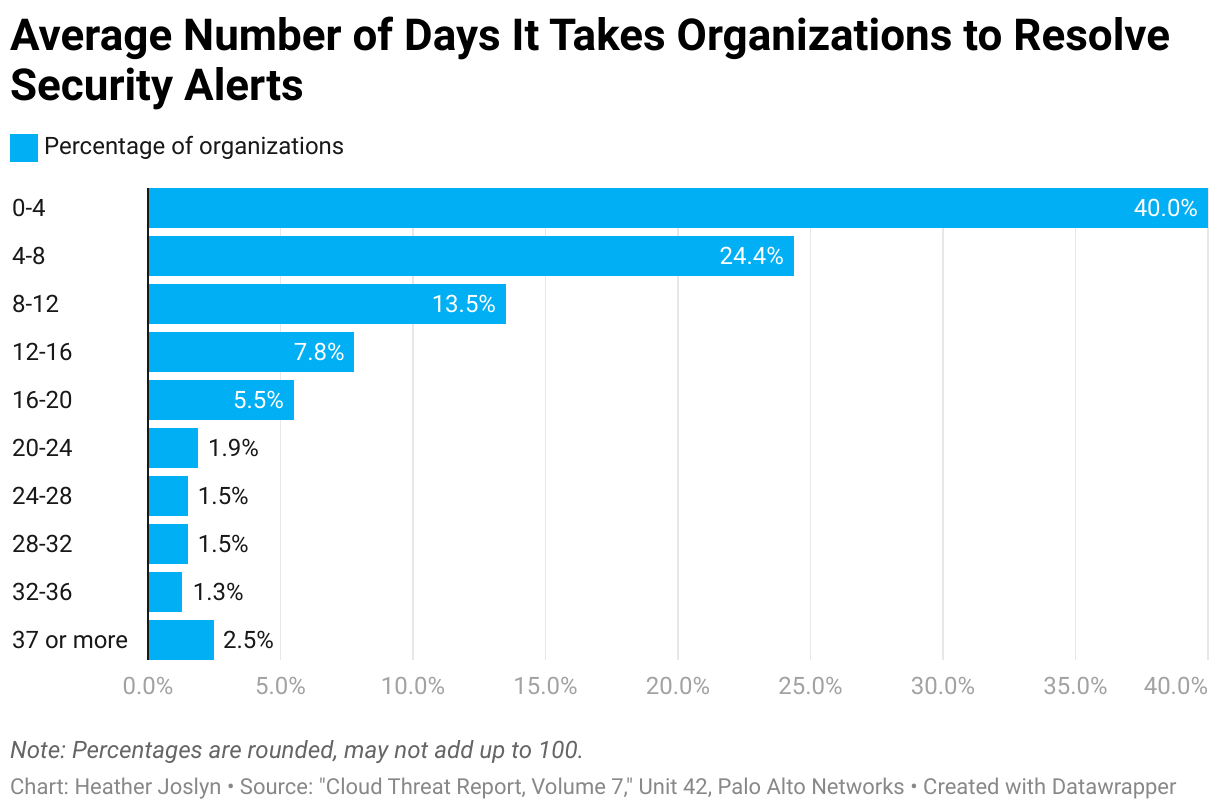
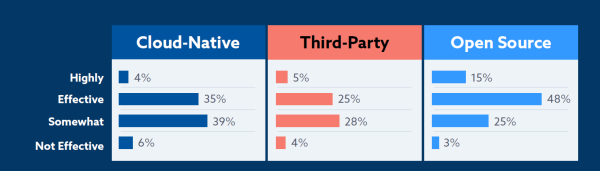
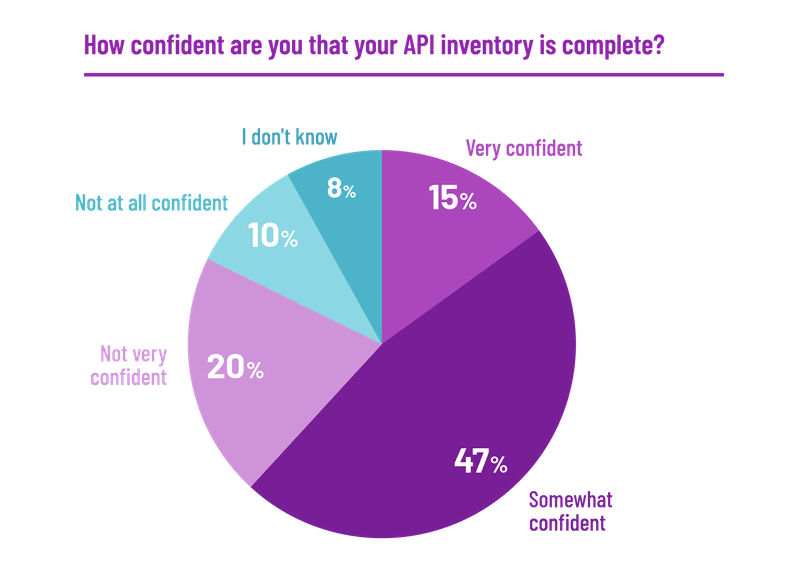
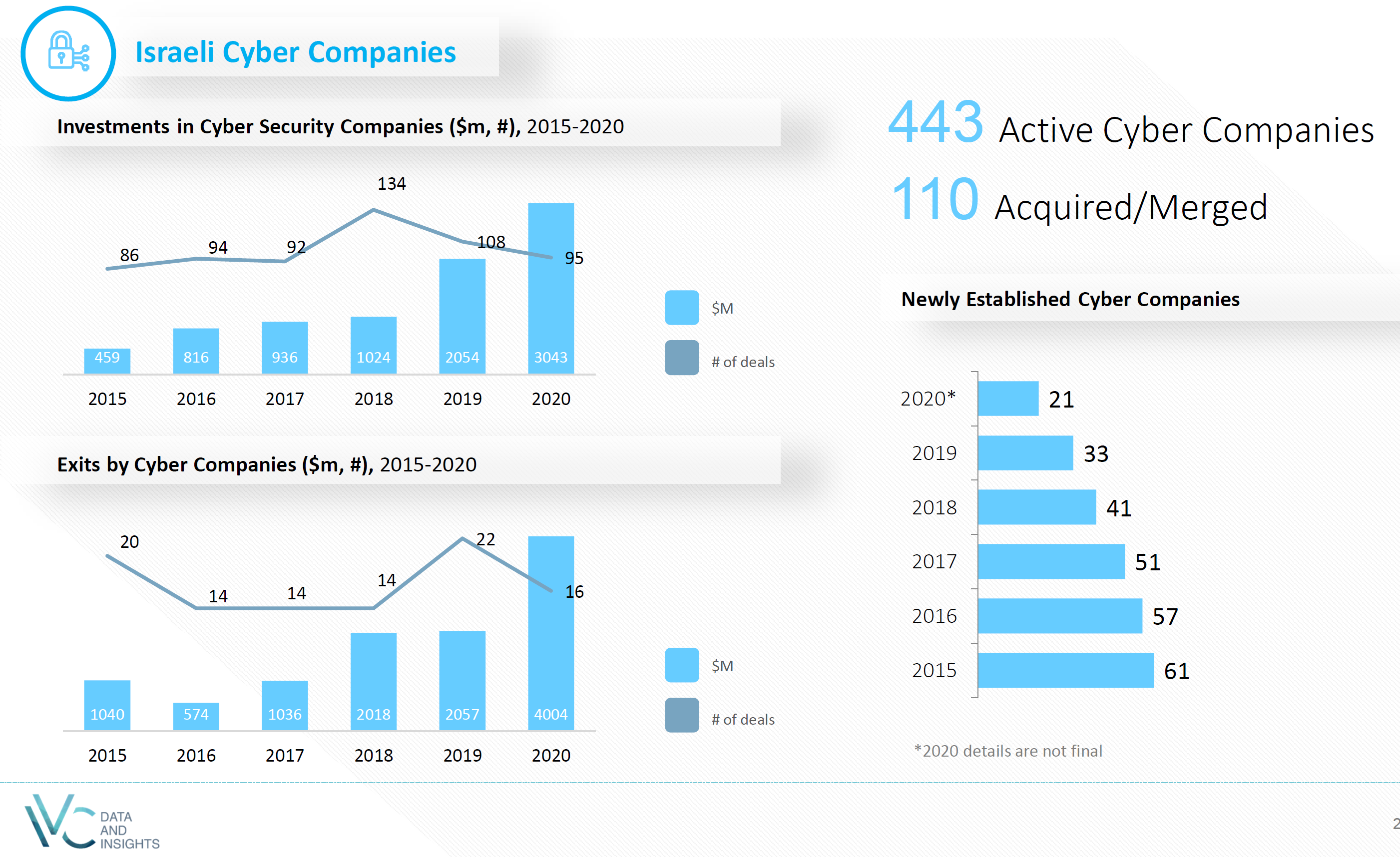
Customer-Facing Incidents on the Rise, IT Leaders Say
Fifty-nine percent of IT leaders said they saw more incidents that affected customers than in the previous year. Even more, 69%, said their organization is not investing in reducing such incidents.