As reported in Anchore’s 2022 Software Supply Chain Security Report, only 22% of the study participants before the Log4j incident reported a moderate or significant impact from a software supply chain attack within the last 12 months. That figure jumped to 35% among those that answered the survey after the Log4j incident. This proves that the community took notice. Perhaps the “impact” was in terms of attention instead of actual costs. Oftentimes, the significance of news events declines as their memory fades away, so we don’t know yet if this will have a long-term effect on security.
The survey of 428 IT and security leaders conducted between Dec. 3 and 22 demonstrates that people believe the Log4j vulnerability (which was publicly revealed on Dec. 10) had an immediate impact.
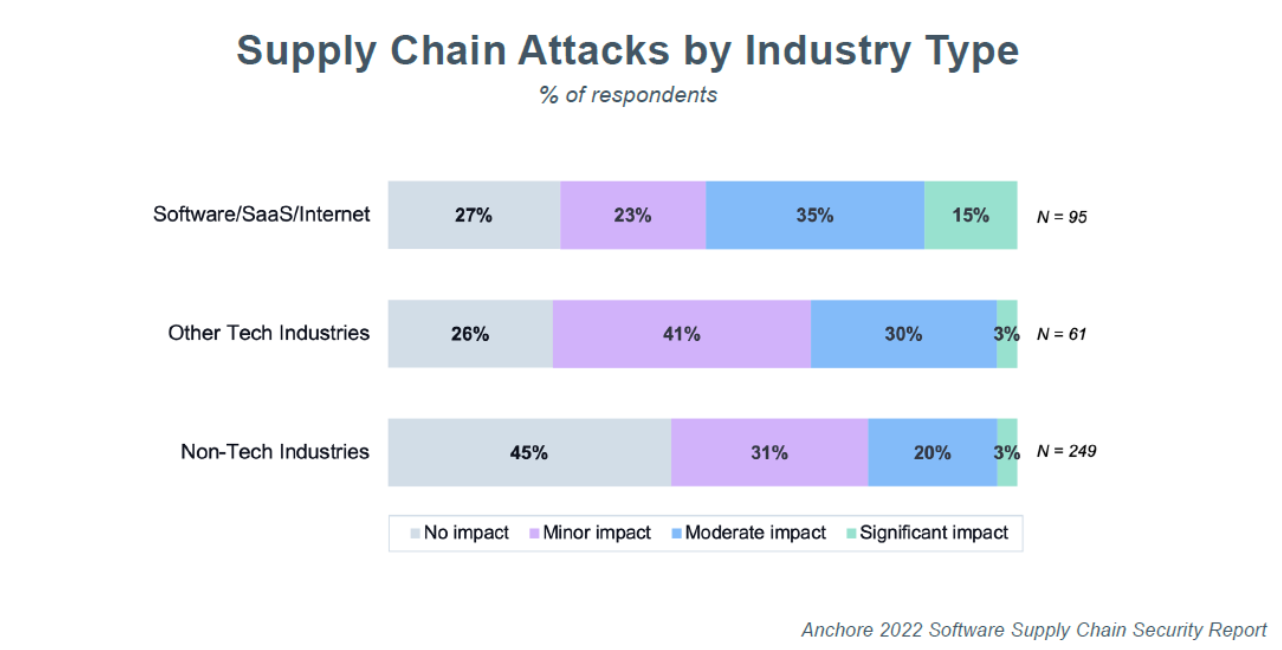
The report also demonstrates once again that software, SaaS and Internet security companies are at the frontlines of the fight against supply chain attacks. Fifty percent of respondents at these types of companies reported a moderate or significant supply chain attack in the last 12 months as compared to just 35% of non-technology companies. Software bills of materials (SBOMs) are a tool in this fight. So far, 36% of the entire survey claims to be creating an SBOM for software they build, but the numbers are much lower in terms of using SBOMs to track their own applications or monitor vulnerabilities.
The complete article can be found here.